How imPAC's Asset Chain Technology Secures Modern Cloud Infrastructure
In response to JP Morgan's recent open letter on third-party supplier security concerns, we examine how innovative cloud security approaches can address today's most pressing risks.
## The Third-Party Problem
JP Morgan's open letter highlighted a critical issue: organizations are only as secure as their least secure supplier. With cloud adoption accelerating, the attack surface has expanded dramatically. Third-party integrations, SaaS applications, and cloud services all introduce risk that traditional security tools struggle to address.
The challenge isn't just visibility—it's understanding how risks compound across interconnected systems.
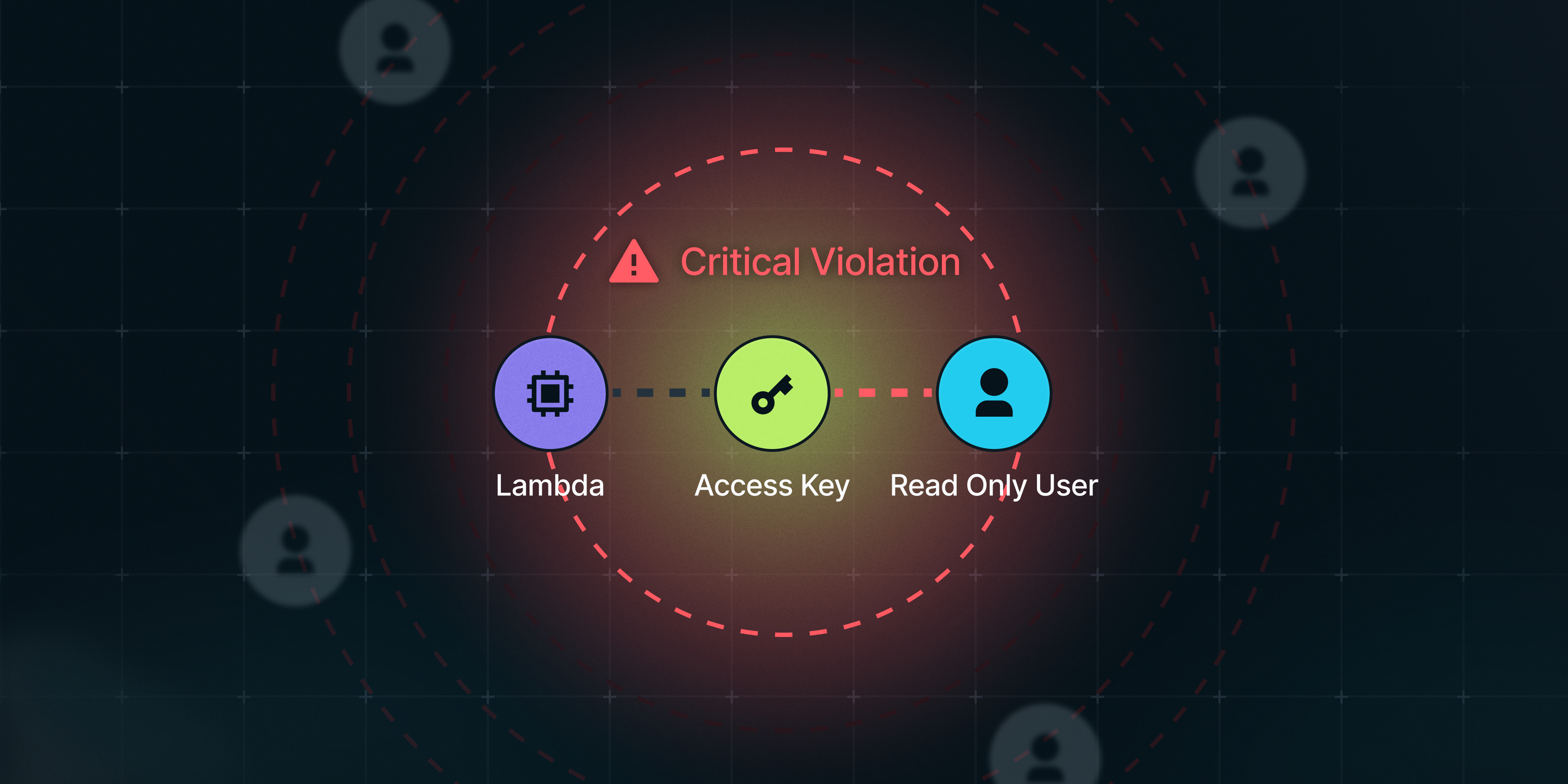
## Asset Chain: A New Approach
imPAC's Asset Chain technology addresses this challenge by mapping relationships, not just resources.
### How It Works
Asset Chain creates a complete graph of your cloud environment:
- **Resources** — Every compute instance, storage bucket, database, and service
- **Relationships** — How resources connect, communicate, and depend on each other
- **Configurations** — The settings that define each resource's security posture
- **Changes** — How the environment evolves over time
### Why It Matters
When a third-party integration is misconfigured, Asset Chain shows you:
1. What data it can access
2. What other systems it connects to
3. What the blast radius of a breach would be
4. How its configuration has changed over time
This context transforms security from reactive scanning to proactive risk management.
## Addressing JP Morgan's Concerns
The open letter called for:
### Better Visibility
Asset Chain provides complete visibility across your cloud estate, including third-party integrations and their connections to your data.
### Faster Detection
Time Machine tracks configuration changes in real-time, surfacing risky modifications the moment they occur.
### Stronger Controls
Compose lets you define and enforce policies that third-party integrations must meet—automatically.
### Comprehensive Evidence
Vault captures every configuration state and enforcement action, creating the audit trail that regulators and partners demand.
## The Path Forward
Third-party risk isn't going away—it's accelerating. Organizations need security approaches that match the complexity of modern cloud architectures.
Asset Chain represents a fundamental shift: from scanning individual resources to understanding complete systems.
---
Ready to see how Asset Chain can secure your cloud?
[Request a Demo](/request-demo)